How Advanced Analytics Can Shore Up Defenses Against Data Theft
- by 7wData
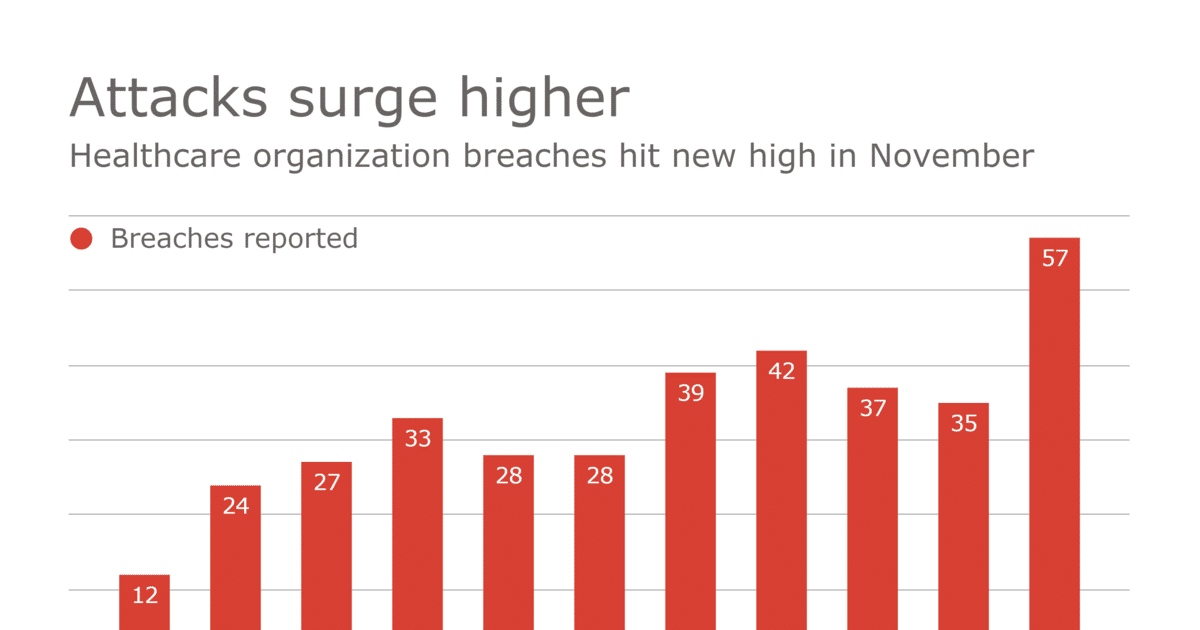
Since cyberattacks on hospital EHR systems have become a topic of nightly newscasts, no longer is anyone shocked by their scope and veracity. What is shocking is the financial damage the attacks are predicted to cause.
During this past June, more than 11 million patient EHRs were breached, making it the year's worst incident according to a study by DataBreaches.net and Prontenus. For comparison, May had less than 700,000 records breached, and records breached in March topped out at slightly more than 2.5 million.
While traditional security filters like firewalls and reputation lists are good practice, they are no longer enough. Hackers increasingly bypasses perimeter security, enabling cyber thieves to pose as authorized users with access to hospital networks for unlimited periods of time. The problem is not only high-tech, but also low-tech, requiring that providers across the continuum simply become smarter about data protection and privacy issues. Medical facilities are finding they must teach doctors and nurses not to click on suspicious links.
However, organizational threats manifest themselves through changing and complex signals that are difficult to detect with traditional signature-based and rule-based monitoring solutions. These threats include external attacks that evade perimeter defenses and internal attacks by malicious insiders or negligent employees.
Along with insufficient threat detection, traditional tools can contribute to “alert fatigue” by excessively warning about activities that may not be indicative of a real security incident. This requires skilled security analysts to identify and investigate these alerts when there is already a shortage of these skilled professionals. Hospital CISOs and CIOs already operate under tight budgets without needing to hire additional cybersecurity guards.
Healthcare security pros need to pick up where those traditional security tools end and realize that it’s the data that is ultimately at risk. The safeguarding of the EHR data is as important, if not more imperative, than just protecting the network or the perimeter.
Some cybersecurity sleuths deploy a variety of traps, including identifying an offensive file with a threat intelligence platform using signature-based detection and blacklists that scan a computer for known offenders. This identifies whether those types of files exist in the system.
However, millions of patient and other medical data files need to be uploaded to cloud-based threat-intelligent platforms; scanning a computer for all of them would slow the machine down to a crawl or make it inoperable. But the threats develop so fast that those techniques don’t keep up with the bad guys; and finally, why wait until you are hacked before trying to identify these threats?
As a result, some healthcare CSOs and CISOs are moving from post-incident to pre-incident threat intelligence. They are looking at artificial intelligence innovations that use machine learning algorithms to drive superior forensics results.
In the past, humans had to look at large sets of data to try to distinguish the good characteristics from the bad ones. With machine learning, the computer is trained to find those differences, but does so much faster with multidimensional signatures that detect problems and examine patterns to identify anomalies that trigger a mitigation response.
Machine learning generally works in two ways: supervised and unsupervised.
[Social9_Share class=”s9-widget-wrapper”]
Upcoming Events
Evolving Your Data Architecture for Trustworthy Generative AI
18 April 2024
5 PM CET – 6 PM CET
Read MoreShift Difficult Problems Left with Graph Analysis on Streaming Data
29 April 2024
12 PM ET – 1 PM ET
Read More




